Just as we were getting ready to launch our Data Breach Monitor, we heard the unfortunate news that fellow Yorkshire based business Vision Direct had suffered a malware attack, which resulted in the loss of financial data of around 6,600 customers.
So we asked ourselves, could we have detected the same attack using our new monitor? The only way to find out was to infect a website and see what would happen…
Purposely (and carefully) infecting a website
At the time of our test, the malicious JavaScript file that was injected into the Vision Direct website was still live at g-analytics[.]com/libs/1.0.16/analytics.js. As is common with these attacks, the domain name and file look close to a legitimate plugin, in this case “g-analytics” could easily be mistaken for Google Analytics. After analysing the code contained in the file we were able to create a fake payment form that was susceptible to the same skimming attack. We loaded the file live from g-analytics[.]com to ensure a fair test:
Below you can see the theft actually happening. As we filled out our fake payment form – just as thousands of people did – all the data present in the payment form was sent to the attackers. Again it does well to hide itself, mimicking a payload similar to Google Analytics. Although the data in the “track” field is encrypted so you can’t see the stolen credit card data, this is easily decrypted on the attackers server.
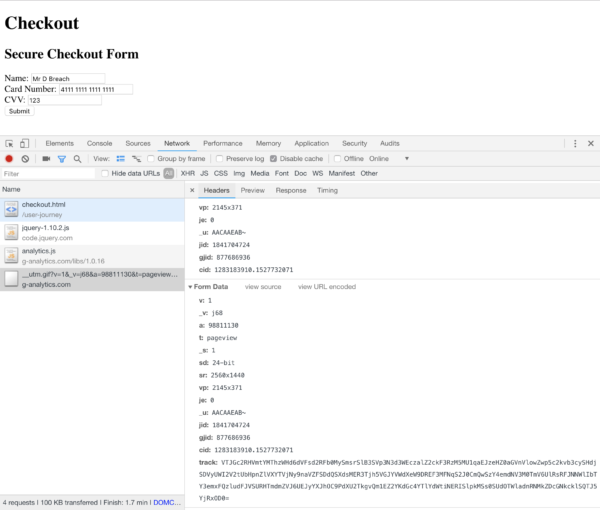
The result
Once our fake, infected checkout form had been added to our new monitor, it took around 5 minutes for us to receive a notification that data was sending to an untrusted host. This gives businesses the visibility of potential attacks in minutes, rather than the average of 12 days to identify a data breach or the five days in the case of Vision Direct.
Similar attacks have made headline news after hitting global businesses such as British Airways (which ran for 16 days), Ticketmaster (which potentially ran for 9 months) and Newegg (which ran for more than a month). Supply chain attacks are incredibly hard to prevent. If you are using third party extensions for marketing, analytics, reviews, comments, etc., you have no control over their security and run the risk of an attack. We have now tested our Data Breach Monitor against several of the biggest attacks and have discovered them all in a matter of minutes.
Not only is there a cost of reputation and compensation, but under GDPR rules there are fines up to €20 million or 4% of annual turnover, whichever is greatest.
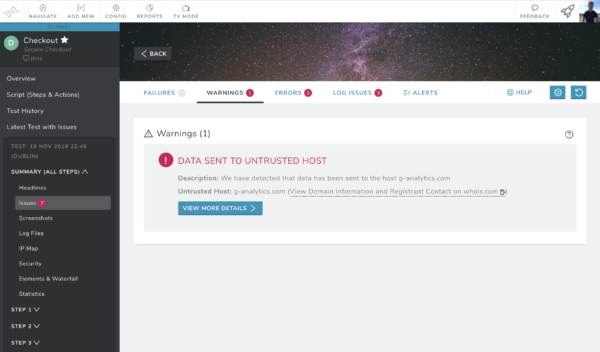
How do I get the Data Breach Monitor?
Data Breach Monitoring is available for all our customers on the River Plan and above. Once it’s configured correctly, you will at least have some comfort you aren’t sending data to places that could compromise your customers and your reputation and if you do, you will know rapidly.






