Just as news hits of two highly critical security vulnerabilities in Drupal – a popular open source CMS that powers 4.2% of known CMS websites – we have expanded our external Vulnerability Scanner yet again with Drupal specific security checks. We now offer peace of mind for anyone with a WordPress, Joomla!, SilverStripe or Drupal site, as well as checks for thousands of known software and configuration vulnerabilities for all major software products and operating systems.
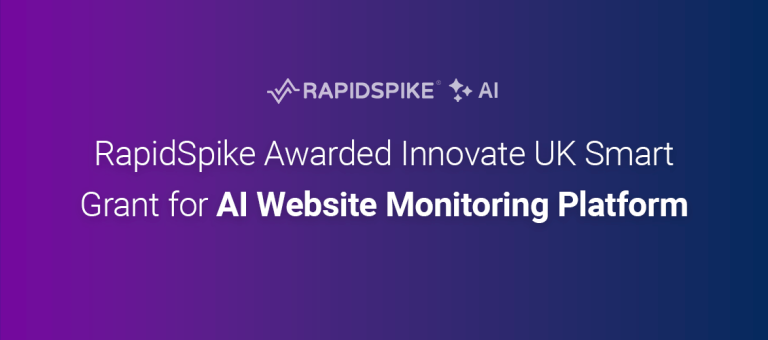
A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised – sa-core-2018-002
If you run Drupal 7.x or 8.x, we recommend requesting a free trial account as we are currently offering a website vulnerability scan for up to 20 websites.
Scans can be created to run daily, weekly, monthly or annually. We constantly update our vulnerability database, so we can automatically detect and notify you of a range of vulnerabilities. It took me 2 minutes to find a website what was vulnerable to the critical bug dubbed Drupalgeddon2, which our system then identified.
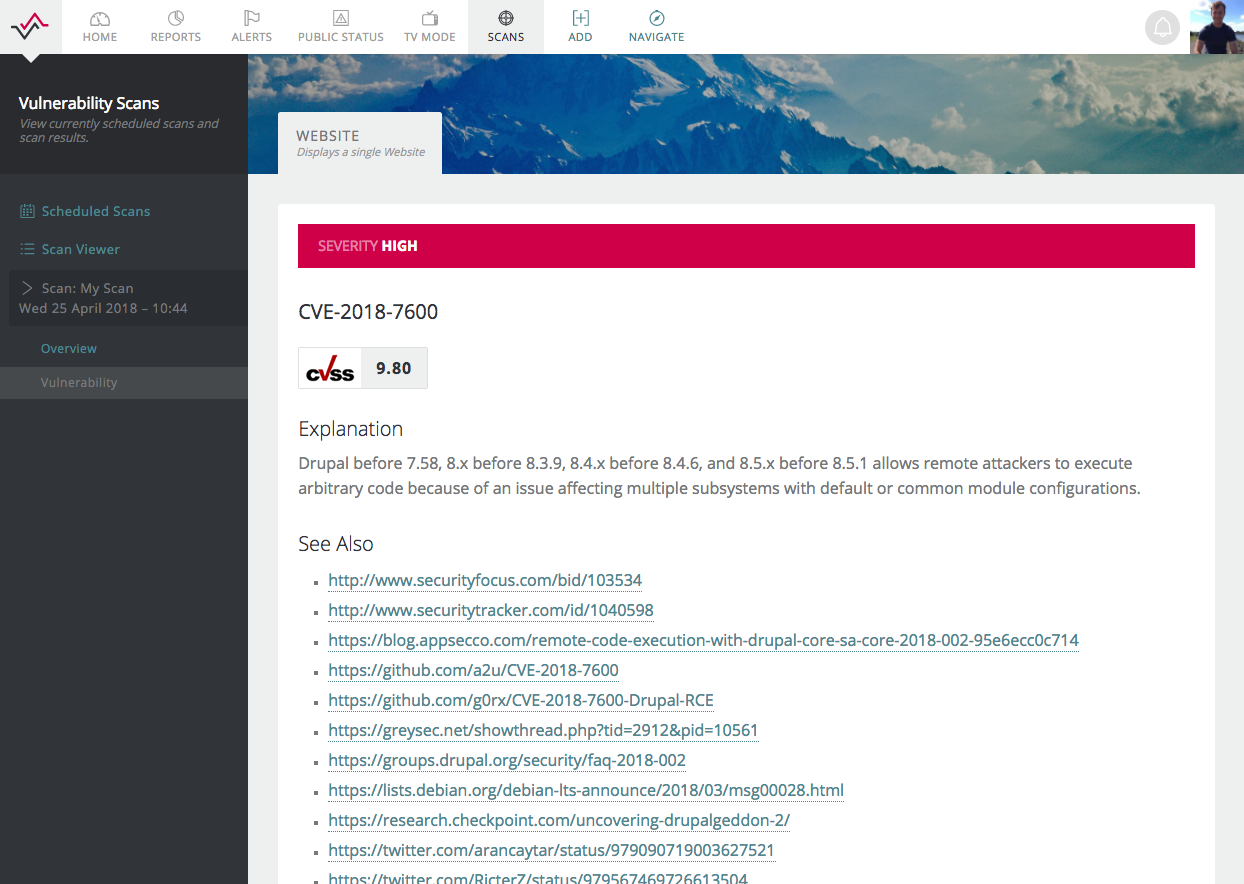
As ever our powerful notification system was able to alert me via Slack:
How do I get started?
Vulnerability Security scans are available as an add-on with any paid RapidSpike plan. Just sign up for an account and then visit the Plan & Billing > Upgrades screen to purchase credits to run your scans.
Like most add-ons, scan credits are paid for monthly. Credits are available in packs of 4 (once a week), 16 (every couple of days) and 31 (daily). Alternatively, speak to our friendly team to arrange a custom plan with as many credits as you need.
Not yet a customer? You can trial our Vulnerability scan software for free by requesting a free trial today.