Once more unto the (data) breach, dear friends, once more. – William Shakespeare.
The retail world is under attack. Hackers across the globe are stealing personal details – including credit card information – on an alarmingly regular basis. This is done by placing digital “credit card skimmers” on compromised e-commerce sites. Hackers are able to access these sites usually through 3rd parties software in the form of JavaScript. Major retailers are prime targets – they are not immune and it’s a becoming a BIG problem for everyone.

They intercept credit card and customer details by placing scripts on retailers sites, sometimes for days sometimes for hours, skimming data and selling it on the black market. Recent high profile breaches include British Airways, Ticketmaster and Newegg. Just last week Vision Direct, a company whose head office is in our home county, Yorkshire, was attacked.

These attacks are not a recent phenomenon – they have been happening for years. Wikipedia lists the first major data breach as occurring to AOL back in 2004 with 92m records stolen. Each year the volume of breaches increases – 2016 recorded a 40% increase on 2015, and 2017 a 35% increase again.
The estimated average cost of a data breach will be over $3.62 million, this does not include the multi-million dollar fines which come after investigation. Responsible for these attacks is a huge criminal network that has operated in the shadows for years. All responsible business owners can do is to take measures to contain the problem.
What can business owners do?
The threat posed by hackers utilising JavaScript as an attack vector is gaining in popularity and with security teams generally working Monday to Friday, weekend attacks are gaining momentum.
Frequently the compromise occurs because of a third-party product, installed in good faith onto a website, is the source of the attack. Third-party products might be advertising tools, customer analytics, live chat, and so on. Just the sort of software most e-commerce sites regularly use.

These JavaScript attacks occur by exploiting a vulnerability on the webserver to gain access to the website and to either inject malicious JavaScript code into an existing file or to edit the HTML of the website to call a new third-party JavaScript file that includes the malicious code. Both of these variants have been seen in recent attacks.
Introducing RapidSpike Data Breach Monitoring
To help stem the tide of these attacks we are pleased to announce the release of our Data Breach Monitor.
Unfortunately, we can’t actually tell you how our Data Breach Monitor works because we need to ensure it remains confidential as we are constantly updating our methods.
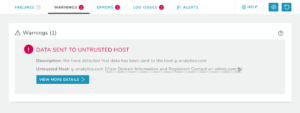
However, in short, we now have a way of detecting data breaches in under 5 mins at the highest level of cover, reducing the average detection time down from 12 days.
RapidSpike visits your website as though we were a normal customer, so we see what the customers see. This means that we can detect attacks designed to target normal users – either via JavaScript from your website or JavaScript from any 3rd party you have installed.
How do I get the Data Breach Monitor?
Data Breach Monitoring is available for all our customers on the River Plan and Above. Once it’s configured correctly, you will at least have some comfort you aren’t sending data to places that could compromise your customers and your reputation and if you do, you will know rapidly. We will be adding new enhanced features over the next 6 months as its an ever-changing landscape.
About RapidSpike
RapidSpike is a Digital Experience Monitoring Platform that interacts with digital platforms exactly as customers do.
Fast, secure and well structured digital platforms achieve better revenue conversion, improve user experiences and reduce global energy consumption.
RapidSpike pinpoints critical platform issues and improvements by collating real time and synthetic data on customer interactions, system performance and security into clear compelling actionable insights.
Sources: