In December 2024, it was reported that the European Space Agency’s (ESA) official online store suffered a Magecart attack aimed at compromising customers’ payment information. The breach involved the injection of malicious JavaScript code into the store’s checkout process, leading to the display of a counterfeit Stripe payment page designed to harvest sensitive data.
Image Source: ESA Website
Domain Spoofing
The attackers employed a technique known as domain spoofing. Domain spoofing is a commonly used tactic by attackers to evade detection. It has been observed in several high-profile Magecart attacks over the years, such as the British Airways breach, where a malicious skimmer siphoned card details to a fake domain, ‘baways[.]com’.
The ESA hackers created a deceptive domain, “esaspaceshop.pics,” closely resembling the legitimate “esaspaceshop.com.” This malicious domain hosted the fake payment page, which was served to customers during the checkout process. The counterfeit page mimicked the appearance of a legitimate Stripe payment interface, making it difficult for users to detect the fraud.
The injected script contained obfuscated HTML code derived from the legitimate Stripe Software Development Kit. This obfuscation concealed the malicious intent, allowing the fake payment page to collect sensitive customer information, including payment card details, without raising suspicion.
Fake Payment Gateways
The breach was identified on December 24, 2024 as the malicious script was actively collecting customer data. Several security firms confirmed these findings, capturing live instances of the fake Stripe payment page being presented to customers.
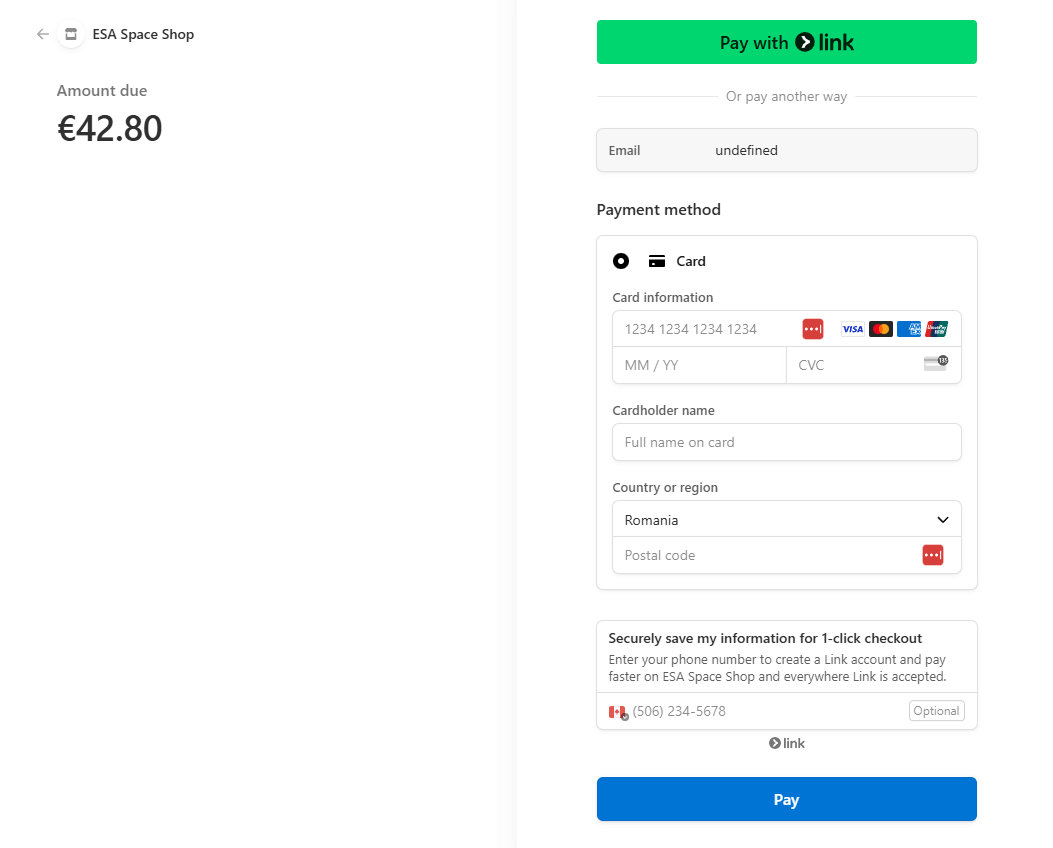
Image Source: Bleeping Computer, 2024
Upon discovery, the ESA took the online store offline, displaying a message indicating that the site was “temporarily out of orbit.”, a pun, despite the reality being much more serious. The agency clarified that the store was managed by a third-party vendor and not hosted on ESA’s infrastructure. This distinction suggests that the breach was confined to the online store and did not affect ESA’s internal systems. It its not yet known how long the attack took place or how many customers were impacted.

Image Source: Forbes, 2024
Magecart Detection Recommendations
This incident underscores the importance of robust security measures for ecommerce websites, especially those managed by third-party vendors. Domain spoofing and the injection of malicious scripts are common tactics used by cybercriminals to steal sensitive information.
To mitigate such risks, ecommerce stores should consider the following measures:
- Regular Security Audits: Conduct comprehensive security assessments of all web applications, plugins and associated third-party services to identify and address vulnerabilities.
- Magecart Detection: Deploy monitoring tools to continuously trace through a website to detect unusual activities, such as unauthorised script injections or domain spoofing attempts.
By implementing these measures, organisations can enhance the security of their online platforms and protect customers from similar cyber threats.