Holiday shopping is in full swing and cybercriminals are preparing their campaigns to maximise their profits this season. Here’s the latest news on Magecart and other website attacks, with insights from our own Security Researcher!
Latest attacks:
- Pipka
- Macy’s
- Black Friday
- Smith & Wesson
- Sweaty Betty
Pipka
Early November, Visa reported a new security alert for an advanced, self-cleaning, JavaScript skimmer named Pipka. First discovered in September earlier this year, the skimmer extracts payment data entered on the checkout page.
Unlike other skimmers, Pipka has an advanced tactic to avoid detection – it can remove itself from the HTML code after it is successfully executed. This self-cleaning tactic makes the code extremely hard to detect by website owners.
This new skimmer means more advanced detection is required to avoid prolonged infection time. Visa give some recommendations in their report, firstly; “Institute recurring checks in eCommerce environments for communications with the C2s provided in this report.” Communications with the C2’s (C2s stands for ‘Command and Control’) means checking the servers the data is sent to. Luckily, RapidSpike Magecart Detection does exactly this! We alert you if we detect data being sent to any untrusted hosts from your website. This reduces detection time from weeks to minutes.
We explain more about Pipka in our blog: Visa Security Alert for New Self-Cleaning Skimmer – Pipka
Macy’s
On November 14th, Macy’s released a Notice of Data Breach informing customers of a data breach on their site macys.com:
“On behalf of Macy’s, we are writing to inform you about a recent incident involving unauthorized access to personal information about you on macys.com. We regret that this incident occurred and appreciate your time to read this letter.”
In the notice, Macy’s explain that on October 15th they were first alerted to a “suspicious connection” between macys.com and another website. Upon investigating this connection, the Macy’s security team discovered malicious code had been present on their site since October 7th.
An unauthorised third-party added malicious code to two pages on macys.com, including the checkout page and the wallet page, accessed through My Account. Alike to other Magecart attacks, details stolen included: names, addresses, phone numbers, email addresses, and payment card details. However, users accessing the My Account wallet on a mobile device or on the macys.com mobile application were not affected.
An anonymous researcher explained to Bleeping Computer how the attack took place: “Attackers compromised the Macy’s website, they altered the https://www.macys.com/js/min/common/util/ClientSideErrorLog.js script to include an obfuscated Magecart script.”
Macy’s acted quickly and removed the malicious code the same day they discovered it. However, this is a popular time of the year for the Macy’s site, so although the number of customers affected is unknown it could still be in the thousands. Macy’s have provided affected customers identity protection services for 12 months free of charge.
Black Friday
RapidSpike Security Researchers have been monitoring Magecart attacks across Black Friday weekend and noticed some common trends:
1. Unsophisticated Attacks
RapidSpike Security Researcher explains: “Following the visa security alert of the sophisticated self-cleaning attacked dubbed Pipka, we saw an increase in unsophisticated attacks, showing that less skilled hackers are finding it easy to attack targets. Another trend across the weekend was an increase in “spray” attacks which compromised as many websites as possible at once and loaded a skimmer. These were unsophisticated attacks as the attackers did not check the URL the skimmer was loaded onto to check for a checkout page and therefore couldn’t steal data.”
2. Fake Checkouts
One of the most interesting discoveries across the weekend involved websites which only accept PayPal as a payment method, were also being infected. Once the form was submitted, data was sent to a server in China and visitors were then directed to PayPal. Over 90 websites have been spotted with this particular attack method and means sites with PayPal-only checkouts need to look into added cybersecurity to ensure customers can shop safely.
3. Repeat Offenders
Across the weekend lots of previously compromised stores were reinfected with skimmers. One example of this is fashion retailer, Sixth June. RapidSpike’s Security Researcher first announced this attack on October 28th with notice given to the company a week beforehand, with no response or action taken. For over two months, skimmers have been removed and readded continuously to the site, the latest attack sees a fake payment page injected onto the site with payment details being sent to an IP in China. Once the form has been filled out, customers are then redirected to another payment page.
Smith & Wesson
On December 2nd, Bleeping Computer reported gun manufacturer Smith & Wesson’s website had been compromised by a Magecart attack. Security researcher Willem de Groot discovered the site had been compromised sometime before Black Friday with a script from the URL live.sequracdn[.]net/storage/modrrnize.js.
Interestingly, this script will load a non-malicious or malicious script depending on their customised target customer. Bleeping Computer explain: “The loaded JavaScript file looks like a 11KB non-malicious script, however if the customer is using a US-based IP address, non-Linux browsers not on the AWS platform, and at the checkout page, the script being delivered changes from 11KB to 20KB, with the Magecart portion appended to the bottom.”
De Groot also made discoveries that this Magecart group had been registering domains imitating his security company:
RapidSpike’s Security Researcher explains: “Due to the attack only launching the malicious script when the specific target customer was active, it makes the skimmer difficult to detect. In the past, we have seen fake Google Analytics domains being used as a disguise for attacks including google-anaiytic[.]com and g-analytics[.]com, which to the untrained eye may be overlooked as the legitimate third-party. It is important to monitor where data is being sent to and to look out for imitations. Using Magecart Detection you will be alerted to any untrusted hosts to your website.”
Sweaty Betty
The latest Magecart attack sees activewear brand Sweaty Betty’s website compromised with a payment skimmer for 9 days. The company sent emails to affected customers explaining that customers who shopped on the website between Tuesday 19th November at 6.42 pm to Wednesday 27th November at 2.52 pm may have had their personal and financial data stolen. This did not affect customers making purchases with saved payment information, Apple Pay or PayPal.
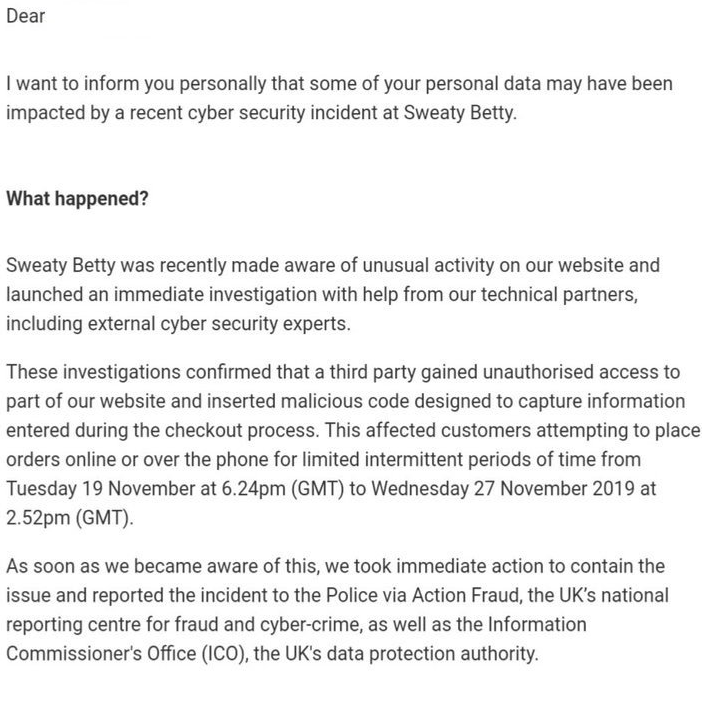
Sweaty Betty reported the incident to the Police via Action Fraud as well as the ICO. The company have not confirmed the data breach on their social media and also took a week to contact customer, causing customer frustration:
RapidSpike recommend affected customers should contact their banks, cancel their card and continue to monitor for suspicious activity.
Recommendations
As the holiday shopping period continues, it is important now more than ever for companies and customers to be vigilant to cyber attacks. Companies should monitor and patch any vulnerabilities on their site which could lead to an attack in the first place and have measures in place to deal with attacks when they happen. It is recommended that customers are wary of different online attack methods. Where possible, use a credit card or PayPal to check out and if a form is loaded before the PayPal checkout, abandon the site. Across the holiday period, it is important to monitor bank transactions carefully.
RapidSpike security researchers have taken the time to investigate all Magecart attacks mentioned. We can confidently say our Magecart Detection would have detected every attack. Magecart detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.