Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus. Recently, we have witnessed some high-profile Magecart attacks including Boom! Mobile, Wisepay, PlayBack Now, and the most recent JM Bullion data breach.
Boom! Mobile
Boom! Mobile, a US-based mobile virtual network operator, has recently been involved in a web-skimming attack on its website, conducted by the notorious cybercriminal Fullz House group.
The site was compromised from September 30th, 2020 until 5th October 5th, 2020. The attack affected the shopping cart page on boom[.]us.
According to Malwarebytes, Fullz House injected a single line of code, which contains a Base64 encoded URL loading an external JavaScript library. The URL is disguised as a Google Analytics script from paypal-debit[.]com/cdn/ga.js. This code is a web-skimmer that skims credit card information entered in the input fields and exfiltrates the data to the cybercriminals.
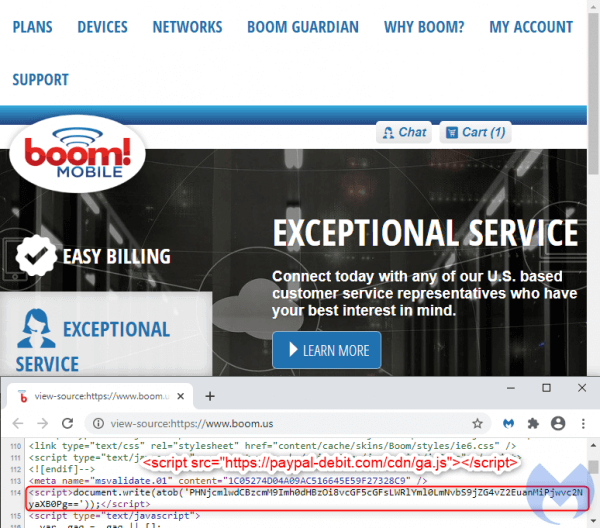
The script used in this attack has been used in previous attacks and is well-known to security researchers. When the attack was first reported, the malicious code was still live and security researchers had been ignored.
In a statement issued by Boom! Mobile after news reports, officials wrote “boom MOBILE deeply regrets this incident happened.” They went on to say “Our shopping cart provider has ensured us our site is safe and the malware has been removed.” RapidSpike would recommend a multi-layered security approach to Boom! Mobile to prevent and quickly detect similar incidents in the future.
Wisepay
On October 7th, it was reported that Wisepay, a service that enables customers to pay for school meals and other school-related costs, had their website compromised.
In a School & Parent Notice, parents at affected schools were told “At some point around 2 October 2020, we understand that a cyberattack occurred in the form of a URL manipulation, meaning that the payment gateway page was redirected or controlled by a bad actor, and your payment card data may have been unlawfully disclosed.”
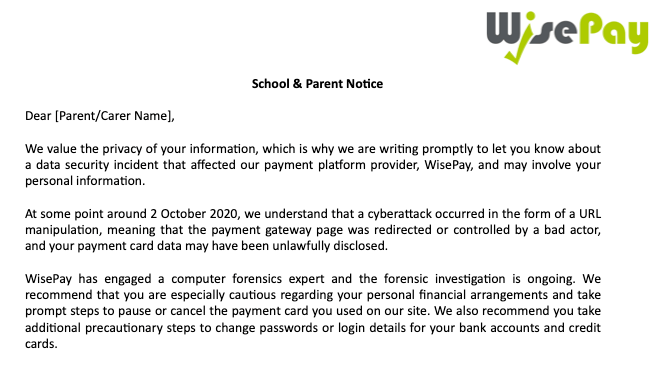
The compromise affected the website between October 2nd, 2020, and October 5th, 2020. A Wisepay spokesman explained that the attackers were “spoofing the Sagepay page to capture card details”. Any customer who accessed the site within the compromised period accessed a spoof payment page. Any information entered into the page was sent to a server in the attacker’s control.
Wisepay has not released the number of affected customers. However, it is believed the compromise affected approximately 300 schools. The website was put into maintenance mode from Monday morning to fix the issue.
Wisepay has informed the Information Commissioner’s Office (ICO), the police about the incident, and parents at all schools.
PlayBack Now
Recently it was reported that Video conference firm PlayBack Now has been compromised in a web-skimming attack aiming to steal customer’s payment and personal data.
The attackers created a typosquatting-based website and injected a web-skimmer into the Magento ecommerce platform within the websites PlayBack Now built for its customers. Approximately 40 PlayBack Now customers have been affected by the attack including the National Association of Realtors, American Diabetes Association, and the American College of Physicians. The number of end-customers who have been affected as a result of these compromised sites is unknown.
JM Bullion
The latest Magecart attack reported in the news was on JM Bullion, one of the largest sellers of precious metals in the world.
In a Notice of Data Security Incident posted on Reddit, the company explains “Through an investigation, we recently determined that malicious code was present on our website which had the ability to capture customer information entered into the website in limited scenarios while making a purchase.”
The company was alerted to “suspicious activity” on July 6th, where they began an investigation using a third-party forensics team. The investigation showed that the malicious code had been present on the website from February 18, 2020, for 5 months until July 17th, 2020, when it was removed. This is a long investigation period for a Magecart-style attack and is an unacceptable timeframe for a company to keep the website live with known malicious code on it. It then took JM Bullion over 3 months to inform their customers, which they did so on November 1st, 2020. This is again an usually long delay for a data breach.
Naturally, customers are not happy. A number of customers have claimed to have large discrepancies in their bank accounts, with others having subscription services set up with their details. The Reddit user who posted the Notice of Data Security states “For all the valuable time I’ll be wasting with my bank – something I feel is owed. Huge breach of security and trust…”.
It doesn’t appear JM Bullion has offered any identity monitoring services to affected customers. They have also not acknowledged the data breach on their website or social media.
The company says the malicious code could capture customer information in “limited scenarios” which form a small portion of the transactions processed on the site. RapidSpike recommends anyone who purchased on the website in the affected time frame should contact their bank immediately and be cautious of any suspicious activity on their account.
RapidSpike security researchers have taken the time to investigate the client-side security attacks mentioned. We can confidently say our Attack Detection would have detected these types of attacks. Attack detection takes less than 5 minutes to set-up and will alert you to any untrusted data on your ecommerce site.